Two-factor authentication and electronic signature for students and staff
University of Žilina







Sensitive contracts, banking transactions, confidential information. Everything in the electronic world can easily be stolen, intercepted or subsequently altered. The use of applied cryptography is a fundamental pillar of a trusted digital world.

We work with state-of-the-art algorithms – Post-Quantum cryptography (PQC), Asymmetric Cryptography (RSA) and Elliptic Curve Cryptography (ECC).

We transfer complex mathematical formulas into real products with practical use.
We have our own dedicated team of cryptographers who follow the latest trends and translate them into customer solutions.

The essence is the use of public and private keys, where the public key is available and is used to encrypt the message. Conversely, a private key is a cryptographic secret that is stored on a secure resource (smart card, HSM module) and can only be accessed by the recipient of the message.
Practical solution of asymmetric cipher is our main activity. By default, we use not only the recommended cryptographic algorithm RSA 4096 (principle of factorization of prime numbers), but also the algorithm of elliptic curves ECC.

The threat of quantum computers based on superconductors, quantum mechanics and qubits is becoming increasingly real. In 2021, the 127-qubit IBM Eagle universal processor was introduced. According to experts, the first functional quantum computer will be built within 20 years.
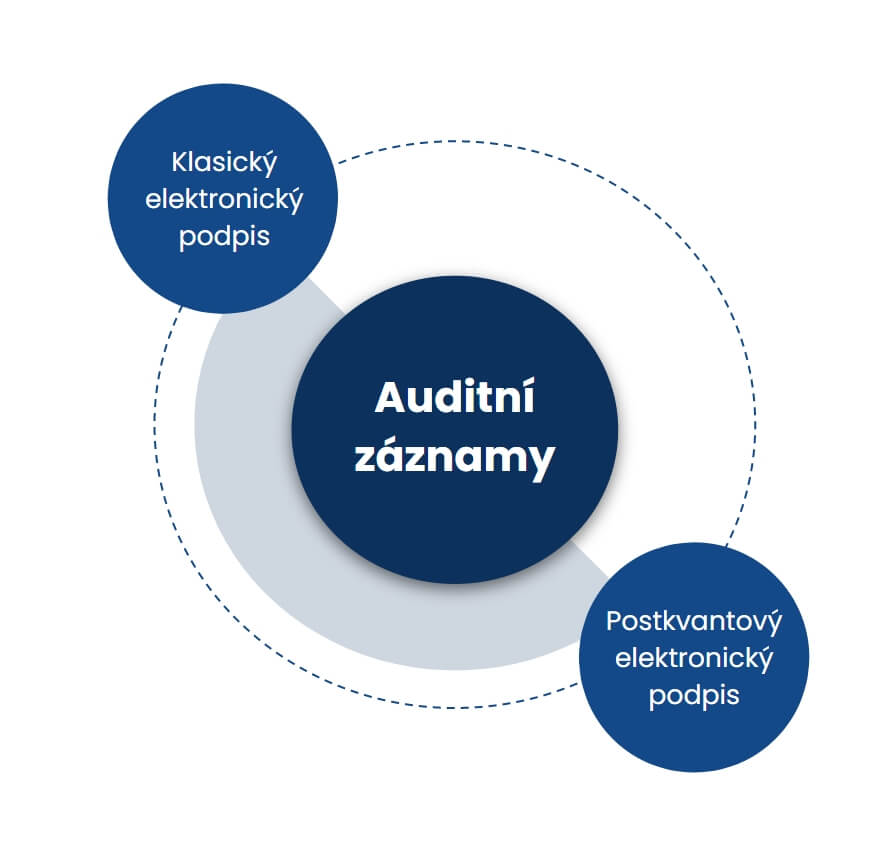
A quantum computer will vastly speed up computing power and can break commonly used encryption algorithms for electronic signature and document encryption. The banking sector and public administration are particularly at risk.

University of Žilina
Erste Group | Česká spořitelna
