MFA for PCs and laptops
Two-factor authentication to Windows, macOS and Linux
Tools to securely log employees into their devices







80% of hacker attacks are caused by credential compromises
Multi-factor authentication is the cornerstone of any organization’s cybersecurity. Instead of a weak password, the employee uses a resource with a stored digital key. For example, a mobile app. Or a smart card. In ProID, individual tools can be combined with each other.

Passwordless
Our methods allow you to log in securely without having to enter a complex password.

Universality
Windows, macOS, Linux… Full coverage of all devices within the organization.

Security
Full control over users and their digital keys with tools for organization administrators.

ProID authentication tools and methods
Protecting access to computers and laptops is the first step to securing your organization. Our tools can eliminate any attempt to break right from the start. Even if the device is stolen by an employee, it is unusable without using two-factor authentication.
Our added value is the mutual compatibility of individual tools and a wide range of add-on modules for administrators of organizations and ordinary users. In addition to logging in, they can also create a qualified electronic signature according to the eIDAS regulation. And also to control the physical devices within the organization – open doors, elevators, printers, etc.
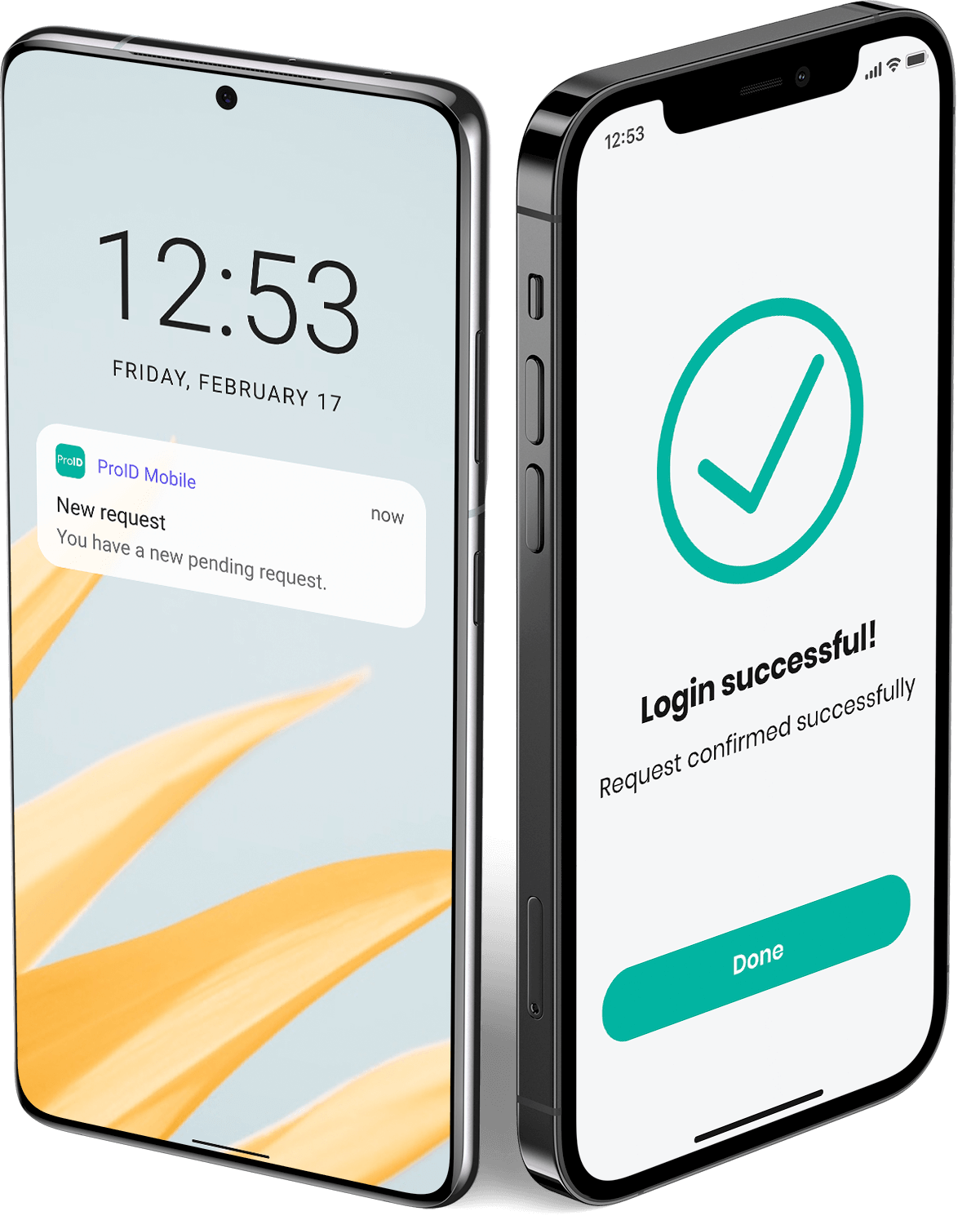
Login to OS Windows using the ProID mobile application

Available tools and methods
Multi-factor login capabilities with ProID


Benefits of using ProID multifactor authentication methods
- Different or complex passwords are replaced by a secure device with a PIN (Passwordless)
- Individual authentication tools (smart cards, mobile applications, Bittron) can complement each other – an organization can use more types of devices.
- In addition to authentication means, we also supply operating modules for administrators and common users.
- The server that handles the certificate lifecycle can be both physical and virtual.
- The delivered solution can be as a service (SaaS) or installed on-premise.
Are you interested in our solution? Contact us