Modern Workforce Identity
Protection employees’ digital identities
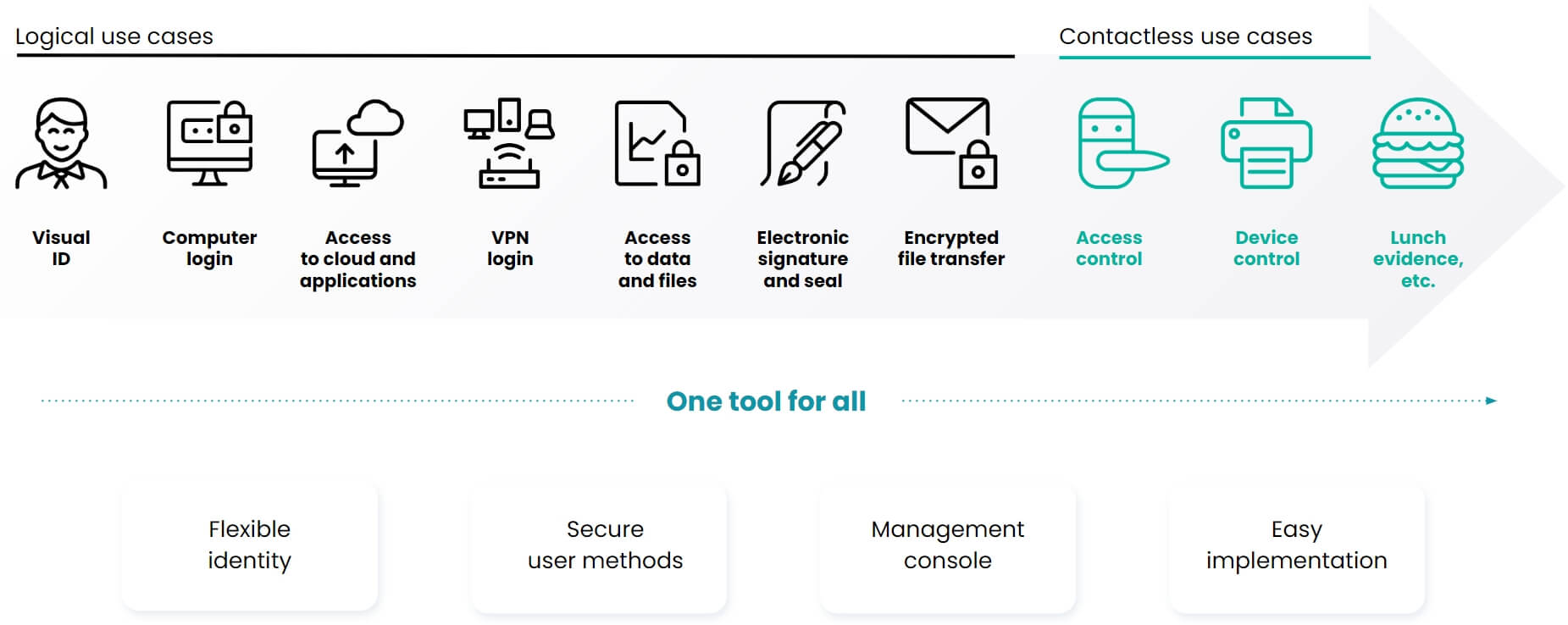
Secure login to systems and computers, protected data access and electronic signature







The weakest point of the organization’s security? Employee.
More and more companies are using various forms of remote work. Or it installs new systems and digitizes its processes. This gives employees access to a wide range of applications and data. At the same time, most hacker attacks are directed through compromised accounts, login data or stolen employee identities. We have the solution. ProID tools.
Identity
A system of digital certificates and assigned tools securely recognizes a specific employee.

Verification
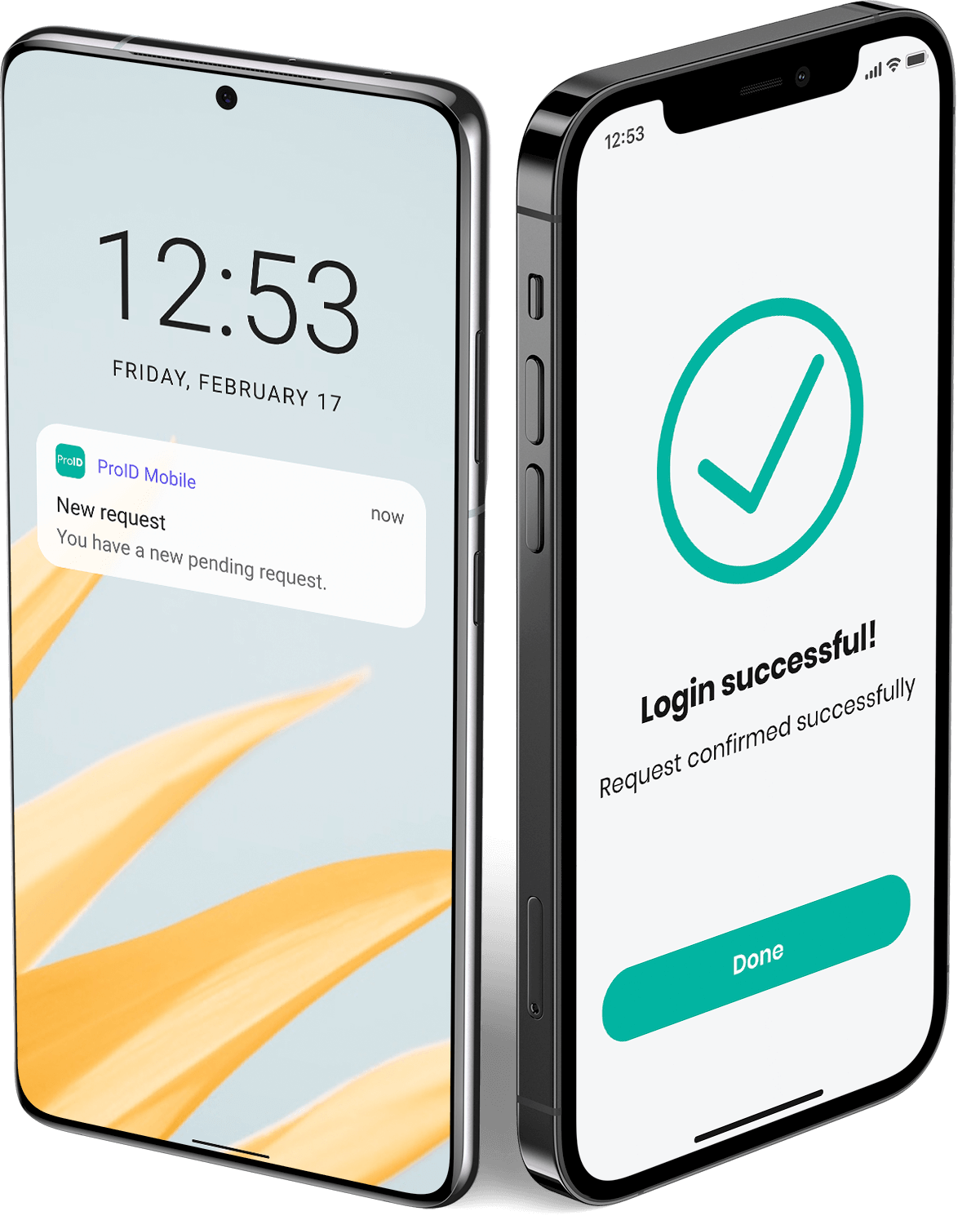
Secure, two-factor authentication technologies are used to log into computers, systems, and applications.

Physical security
Our tools can also provide physical security for interiors and devices.

Secure login to internal systems
Protecting access to computers, systems, and data storage is an essential step in securing an organization. Our tools can eliminate any attempt to break right from the start. Even if the device is stolen by an employee, it is unusable without using two-factor authentication.
Our solution covers most customer-required scenarios and allows authentication to supported VPNs, network elements, firewalls and admin consoles, such as Cisco VPN, OpenVPN, F5, FW CheckPoint, FW Fortigate and many others. The same as in MS Windows and macOS. We also support two-factor login to various office applications (MS Office, G Suite, Salesforce and many others).




Free brochure
Protecting your organization’s infrastructure with PKI and building Certification Authorities

Security of premises and employee records
Operating theatres, laboratories, premises for discrete production. Everything that should be accessible only to a defined group of employees. With ProID, your organization will always have control over who enters where. The contactless chips in our cards can be connected to most attendance systems and other employee applications.
In addition, other internal systems can be connected to our tools. Registration of meal vouchers, control of elevators, control of office equipment or registration in the logbook.
ProID offers a comprehensive solution for secure access to company data
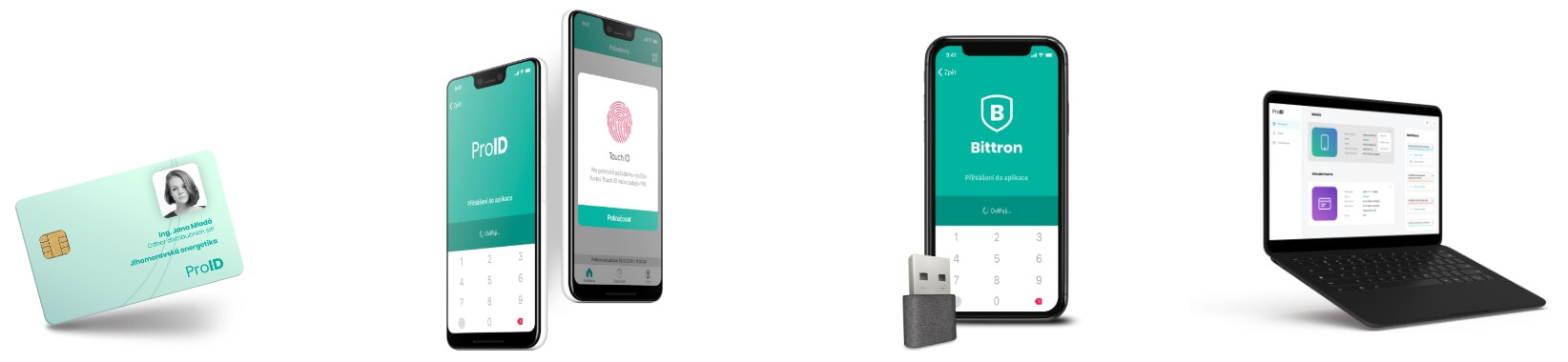
Employee Digital Identity you´ve never seen before


ProID authentication tools and modules
These are ProID smart cards, USB token and ProID Mobile mobile application. The basic features of all products are reliability, absolute security, simple operation and a pleasant user environment. In addition, ProID chip cards can create a qualified electronic signature according to the eIDAS regulation.
Digital certificate management modules
All tools can be supplemented with add-on modules that allow organization administrators to automate complex operations over digital certificates and cryptographic keys. They help users update them and prevent them from expiring.
ProID is a comprehensive platform for secure digital identity for employees and organizations.
Tools available for employees
Our projects
Are you interested in our solution? Contact us