“Protecting your organization’s infrastructure with PKI and building Certification Authorities” – brochure
All about PKI and CAs, their implementation and use cases. A comprehensive guide for organizational infrastructure administrators with descriptions of technologies and best practices.
Are you interested in PKI technology and building your own certificate authorities? Would you like to know how they can help you secure your organization’s infrastructure? We have prepared this brochure just for you. In 20 pages, we’ll introduce you to the basic types of PKI infrastructure, how to implement internal CAs and how to link them to authentication tools and digital certificate management modules.

To download the brochure, fill in the form
Why build your own PKI or CA?
The digital world is becoming more connected and more dangerous at the same time. On the one hand, there is the pressure to maximize accessibility (from the home office, offsite or mobile devices). On the other, organisations are exposed to increasingly advanced cyber threats. The situation is not made any easier by the move of services to the cloud and the ever-expanding use of the Internet of Things (IoT).
At such a time, we are faced with a real problem: how to ensure that only the authorised user (or device) can access the data, while at the same time not burdening them with complex authentication methods? Clearly the best solution is PKI (Public Key Infrastructure) technology.
Brochure content:
- PKI as a tool for protecting an organisation’s digital identity
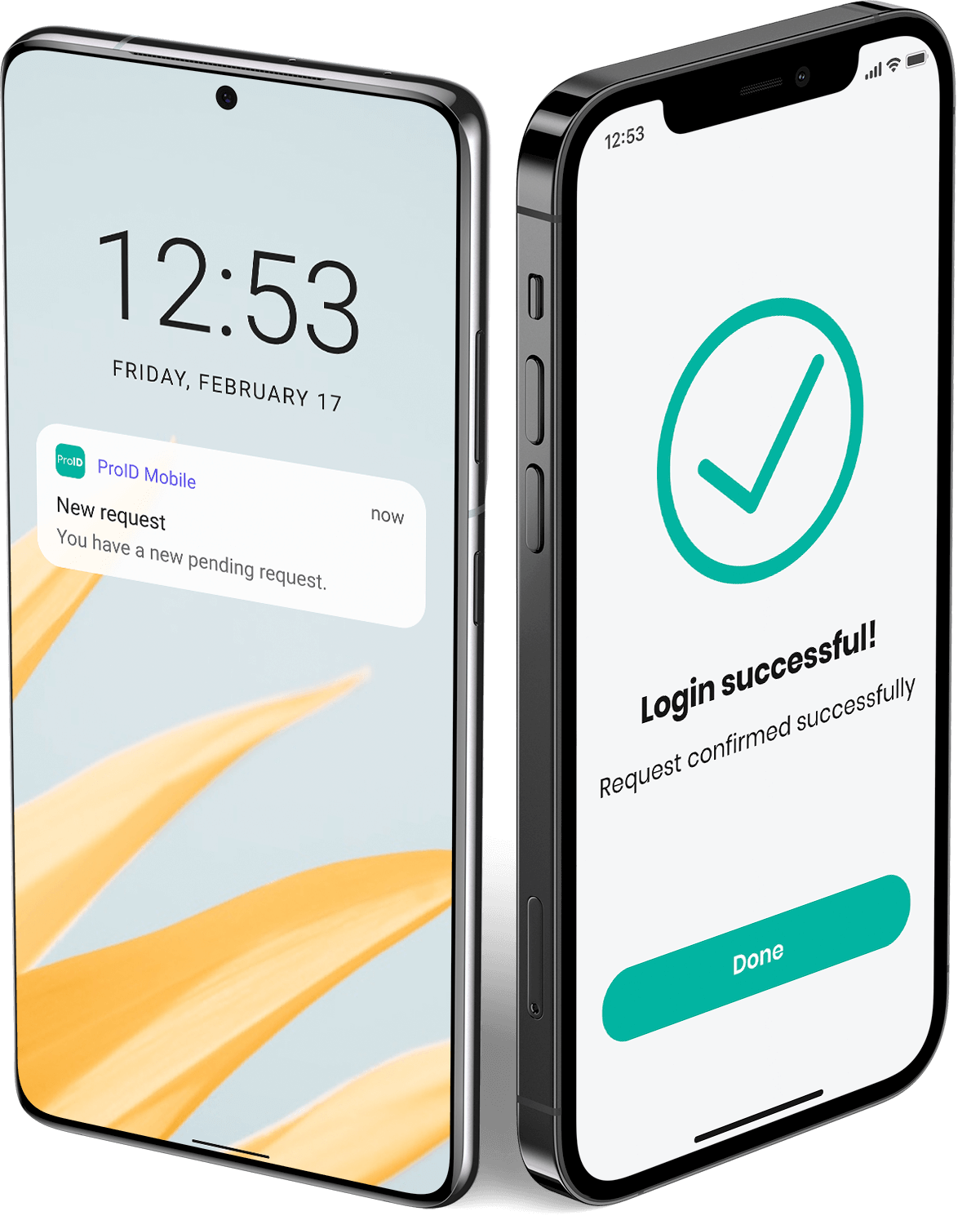
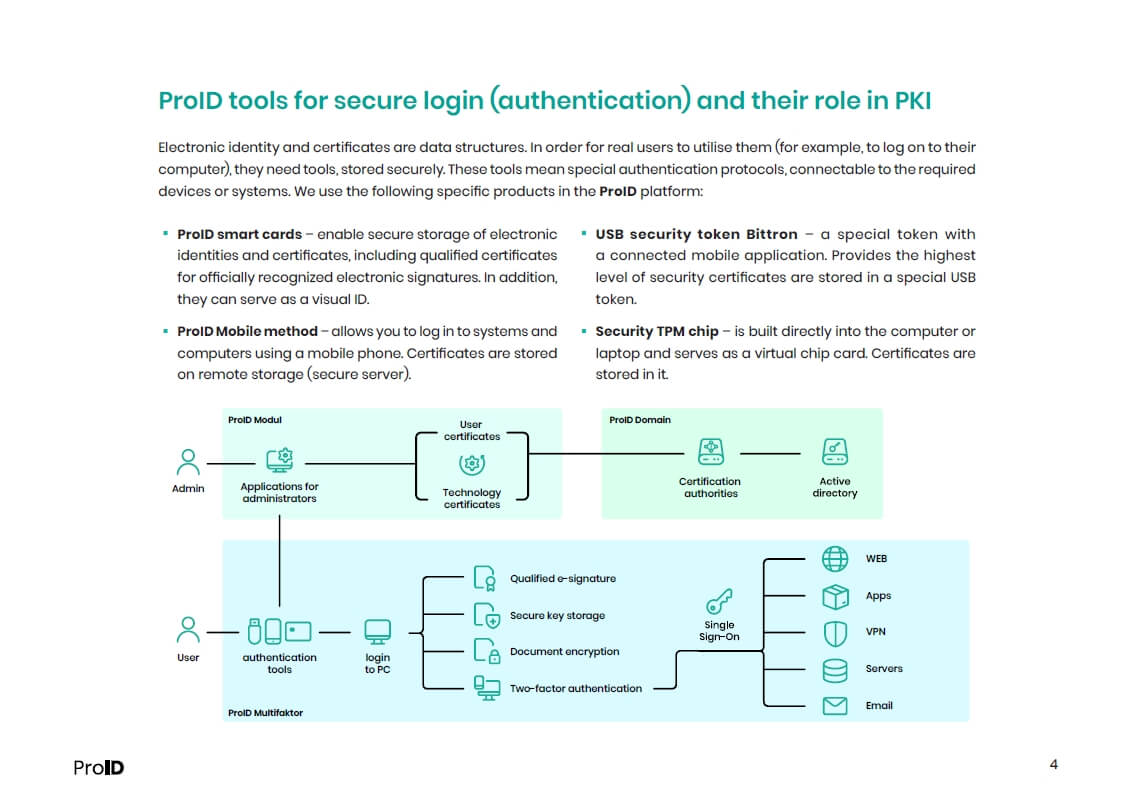
- Secure login (authentication) tools and their role in PKI
- Basic Domain PKI with Certificate Authority
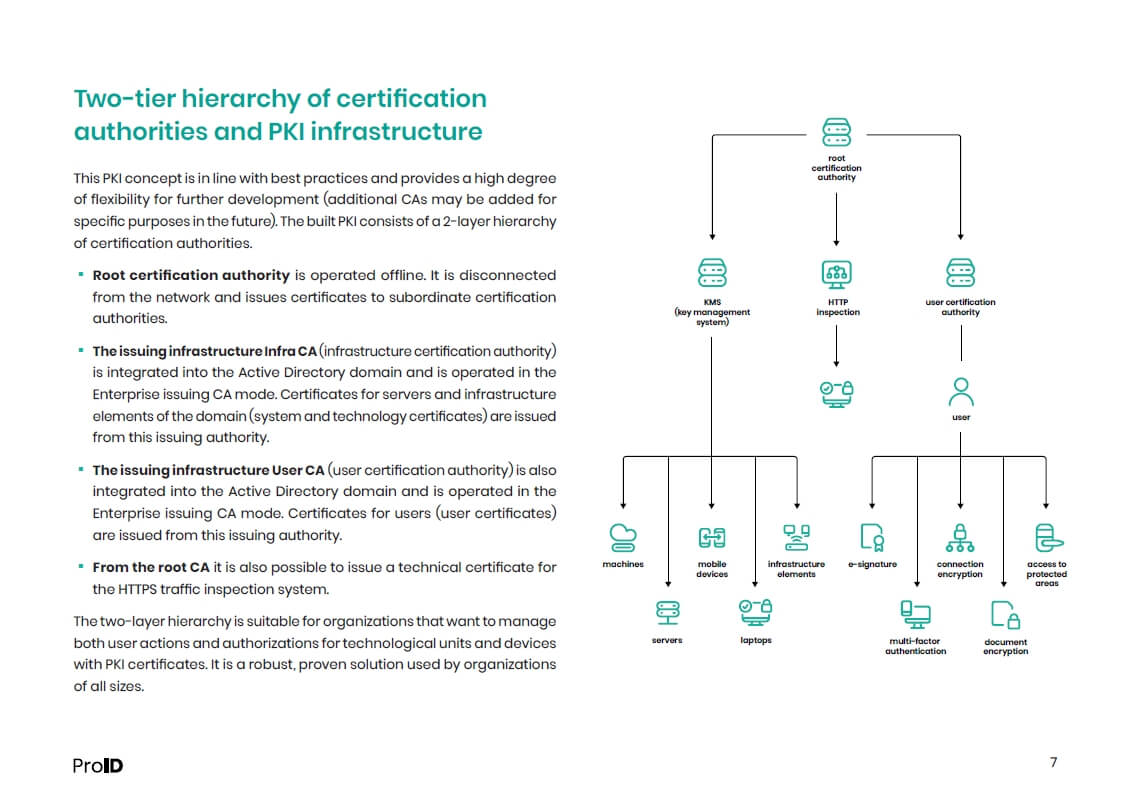
- The two-layer hierarchy of CAs
- Multiforest structure of PKI and CAs
- Separation of CA security perimeters
- PKI Certificates and their lifecycle
- Incident escalation and user roles within the PKI
- HSM servers for cryptographic key protection
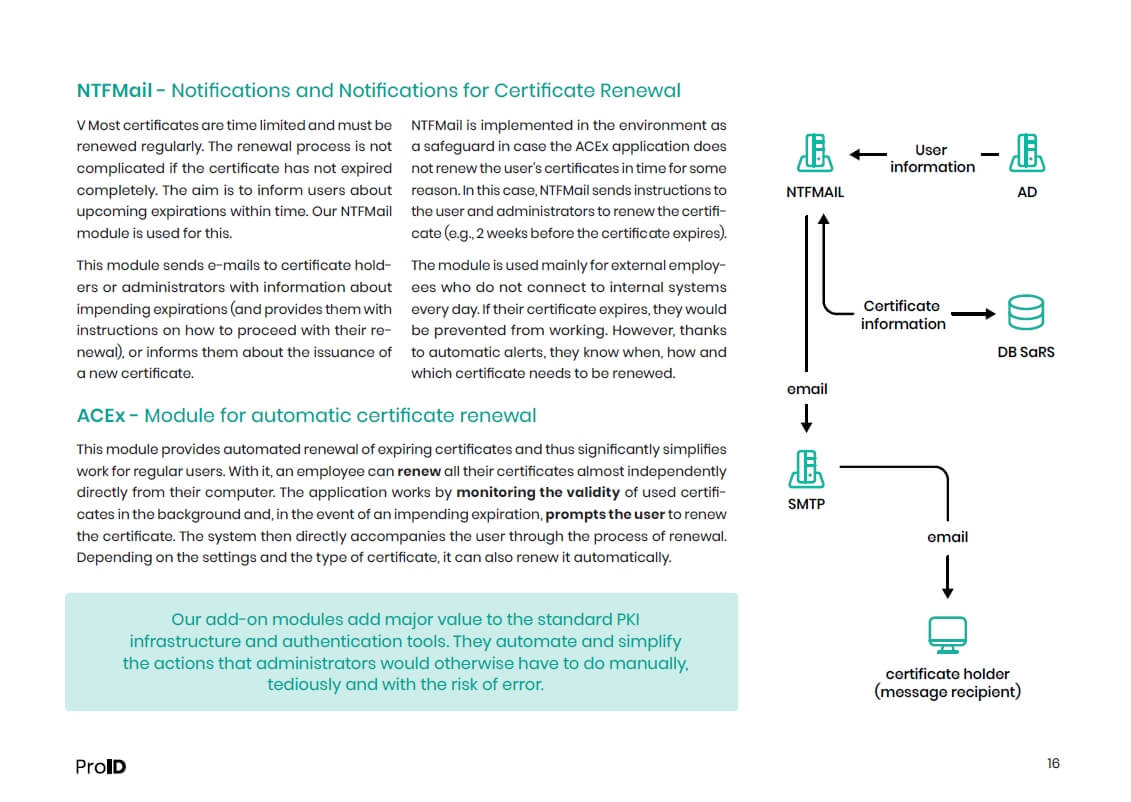
- Special modules for certificate lifecycle management
- Security, backup and auditing