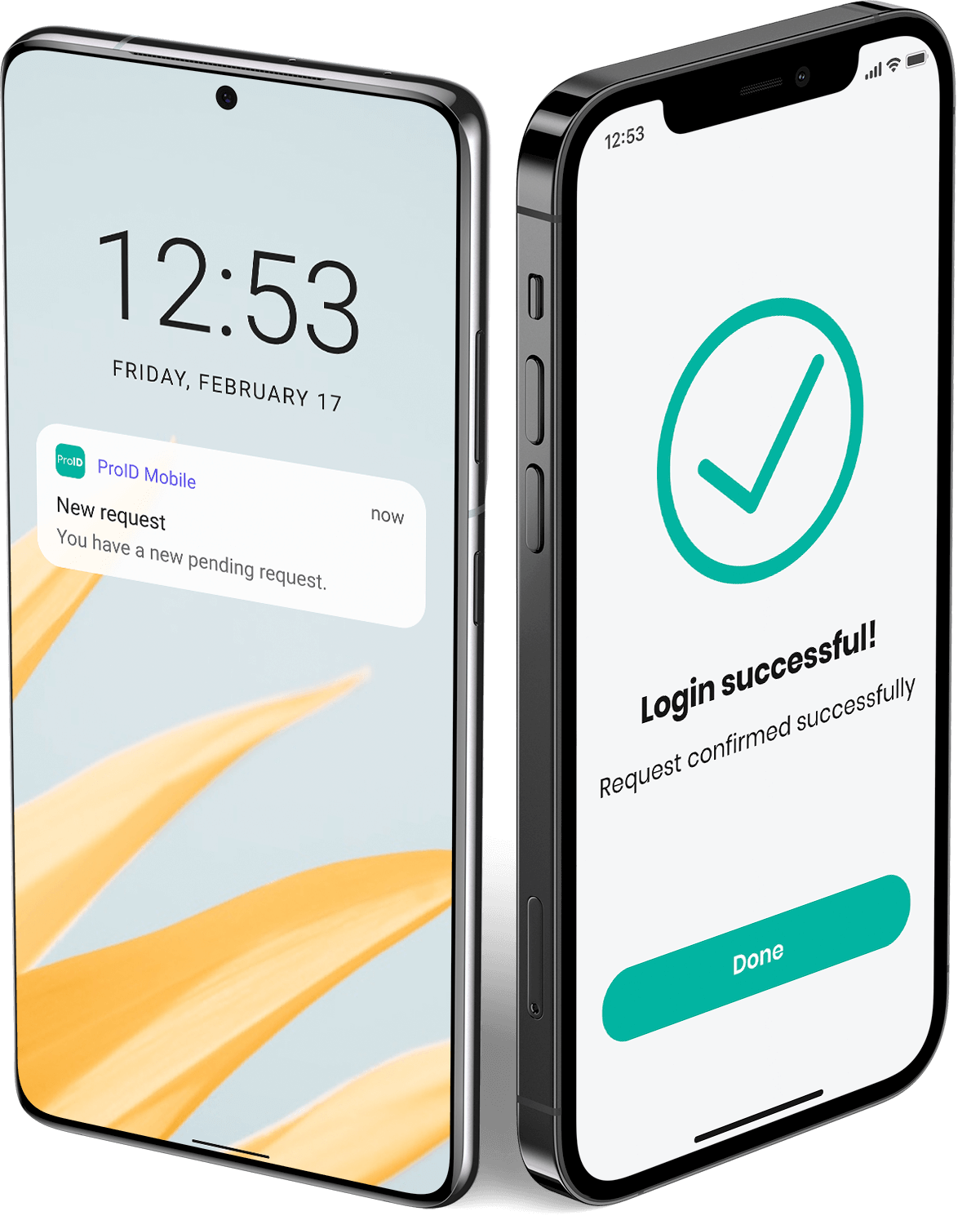
Tools for users
ProID Mobile
Multifactor authentication by Smartphone
Securely log in to computers, VPNs, and business systems with the mobile app

Protecting access to corporate data has never been easier
One PIN, Face ID, or fingerprint. Secure two-factor login to systems and electronic services that everyone has with them always and everywhere.
Smartphone as an Access Key
80% of hacker attacks are caused by the breach of employee credentials to company systems and devices. Our mobile app offers a simple but functional solution – the mobile phone becomes a real digital key to company data.
ProID Mobile is an authentication method that uses an external certificate store with keys and as a login tool there is a mobile phone with an application installed.
This has a lot of advantages, especially for ordinary users. While you can forget or lose your card, everyone always has their mobile phone with them.
Watch the recording of our webinar “Smartphone as an Access Key” to learn all about our new security app.


A new dimension in corporate security
Main usage scenarios
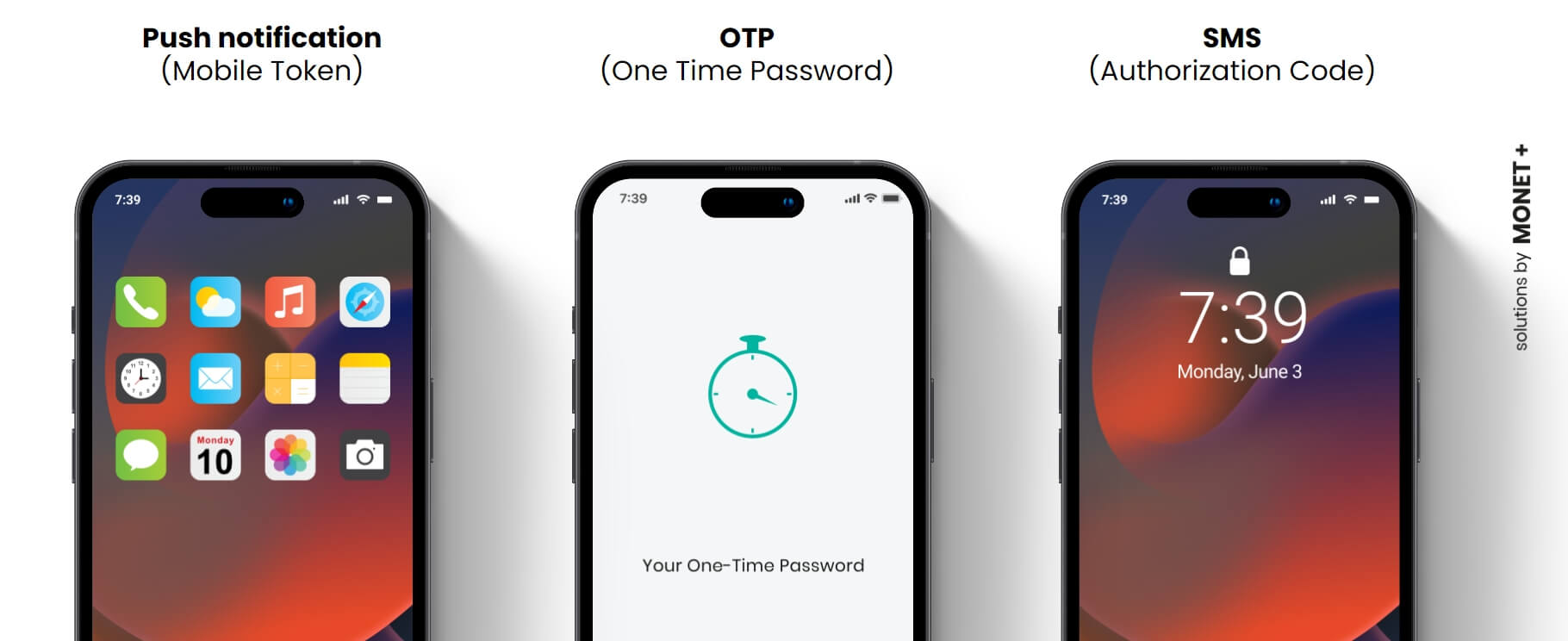
Authentication possibilities – Push, OTP or SMS

ProID Portal – Web interface for Device management
ProID Mobile is not only an application, but also a complete administrator interface. This web interface is the ProID Portal and allows you to offer ProID tools as a SaaS cloud service using external HSM servers and Microsoft Azure technology.
In the portal, it is possible to easily set various permissions for specific users, methods, certificates or connections between devices and systems. Whether it’s users or administrators, everyone will find what they need.
Integration into 3rd party apps
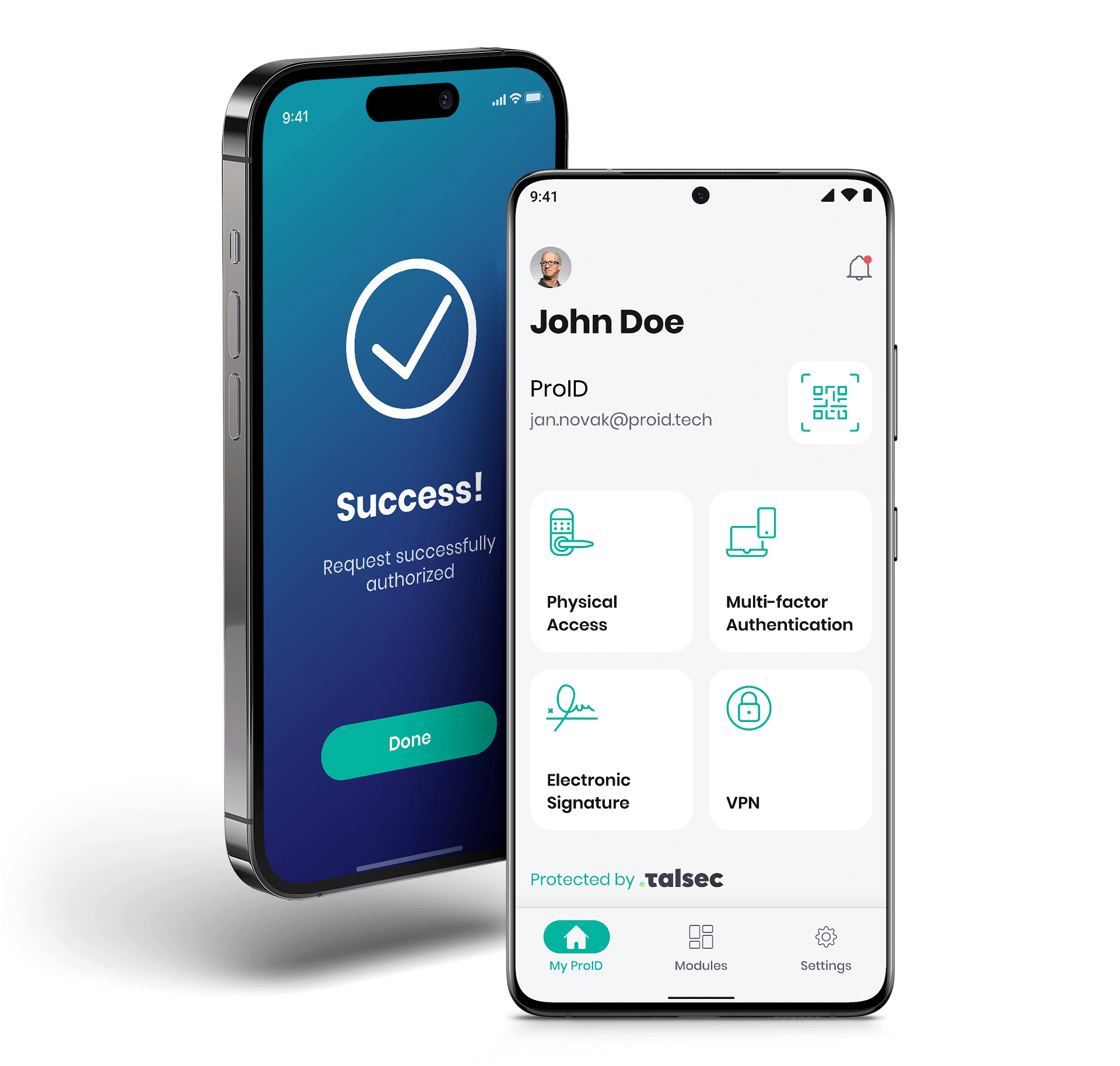
Security by Design
The application has an integrated security RASP module (Runtime Application Self-Protected), which actively protects the mobile phone and installed applications from attacks, monitors their security or detects malware and other threats.
The user’s cryptographic material is stored on an external HSM module, which is part of both the cloud service and the on-premise installation.
The entire system is delivered as a cloud service (SaaS) or is installed inside the organization as an on-premise solution.
Are you interested in our solution? Contact us