Mandatory legislation
Implementation of tools and security management for NIS2
Tools, processes and security policies

We will help you solve the processes and technologies for NIS 2. Fast and comprehensive.
We offer many years of experience from dozens of implemented projects that were in compliance with the strictest legislation (NIS 1, eIDAS, Cyber Security Act, etc.).
NIS 2 as the basis for EU and your organisation’s cybersecurity
Over the past few years, the number of cyberattacks on critical government organizations and private entities has increased dramatically. These attacks caused long-term outages and huge financial damage.
The new EU Cybersecurity Strategy (NIS 2) aims to improve tools and resources to ensure security at the level of the organisations themselves.
The NIS 2 Directive will be mandatory and will apply to 150,000 entities in the European Union. It will also include completely new industries, such as the food industry and manufacturing companies. The maximum fine for non-compliance will be €10,000,000, or 2% of the company’s total worldwide annual turnover.
Compliance with NIS 2 requires detailed knowledge of processes, legislation and technical solutions. We have it.

Certification
Our solutions, the companies involved and our consultants meet Czech and EU certifications.

Experience
We have implemented dozens of projects for the largest authorities, hospitals and small companies.
Hinterland
We have offices all over the Czech Republic and dozens of cybersecurity experts.
We can help you secure your organization and comply with mandatory regulations

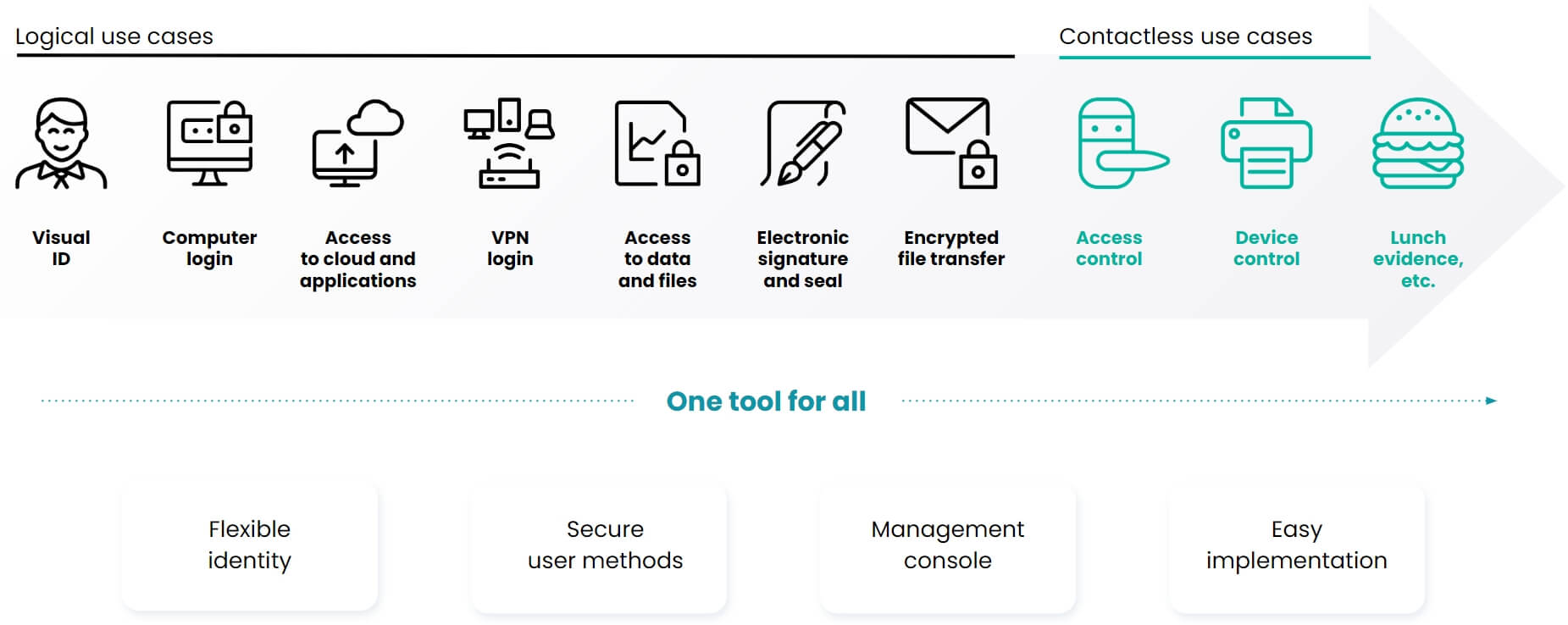
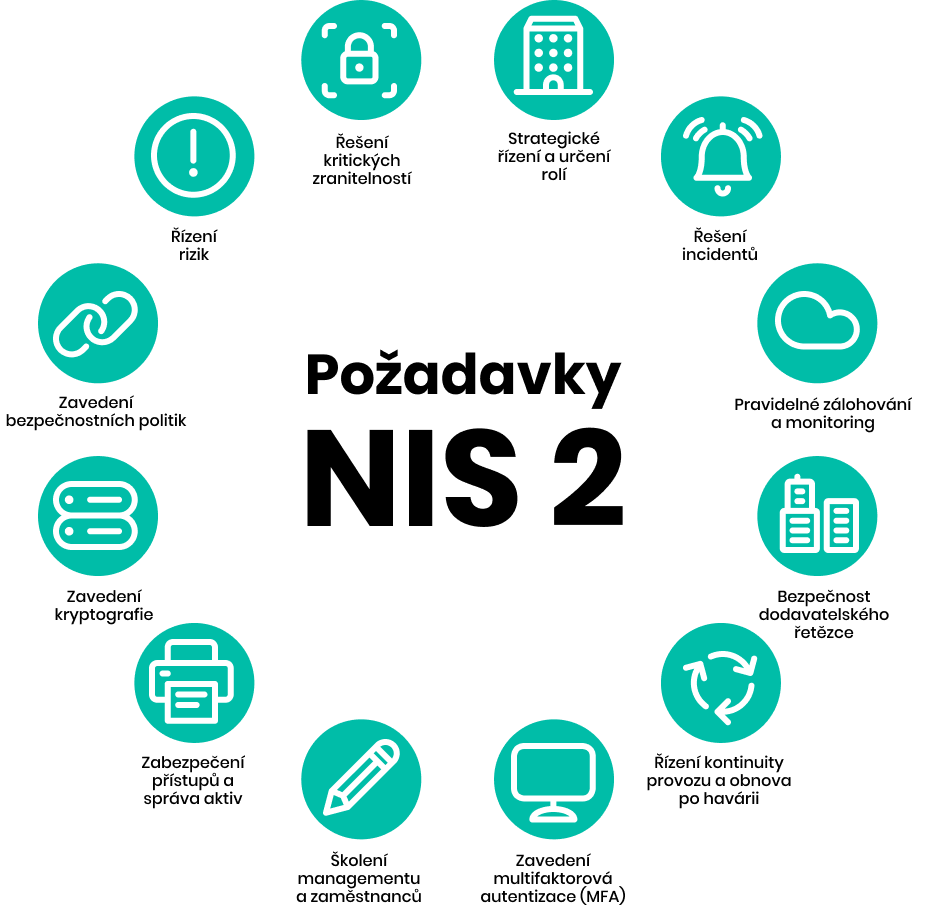
Technical solutions for NIS 2
- Implementing Two-Factor Authentication
- Implement strong cryptography and endpoint encryption
- Securing networks, applications, systems, and software
- Ensuring the physical and digital security of IT infrastructure
- Detection and assessment of cyber threats
- Ensuring data backup and eventual recovery
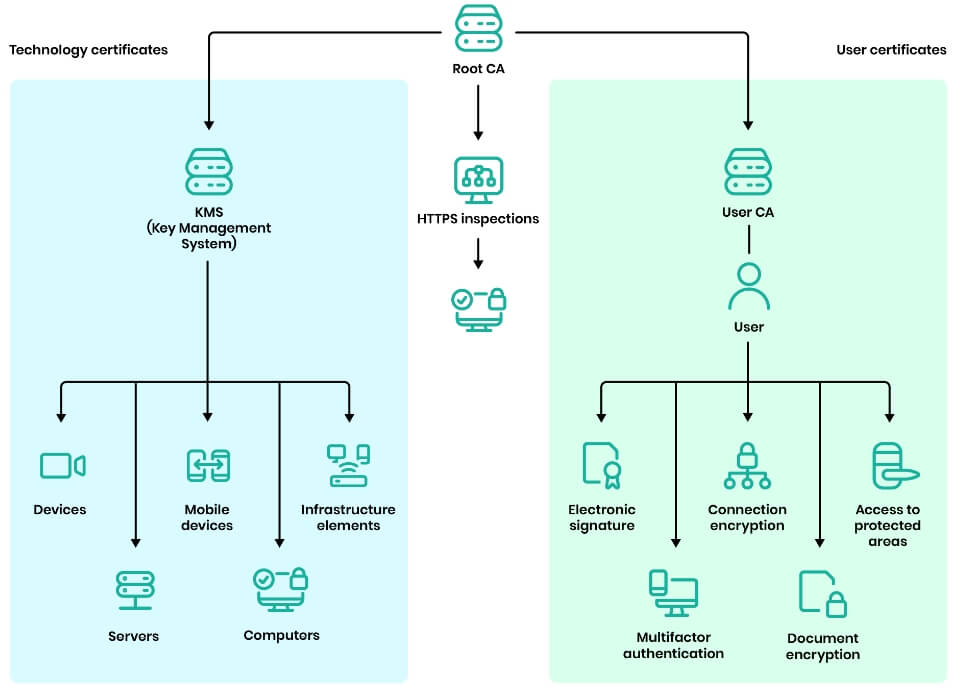
Construction of PKI infrastructure and Certification Authorities
PKI (Public Key Infrastructure) is a technology for managing digital certificates and for cryptographic operations (electronic signature, communication encryption, endpoint encryption, etc.). PKI is based on the Certification Authorities system. Within organizations, we most often build a two-tier PKI hierarchy, where one is the root Certification Authority and the others are subordinate.