PKI infrastructure for qualified electronic signing
Chancellery of the National Council of the Slovak Republic








PKI (Public Key Infrastructure) is a technology for managing digital certificates and keys. We build it on modern cryptographic algorithms and develop a number of add-on modules. These allow you to automate complex processes over certificates and prevent security incidents. The basis of our solution is the construction of certification authorities.

Building domain PKI and building certification authorities including operational, emergency and security documentation.

Construction of multi-tier certification authorities that allow future development and implementation of additional modules.

Physical security of the servers used as well as stored data on the HSM (Hardware Security Module).
Within organizations, we most often build a two-tier PKI hierarchy, where there is one root certification authority and two subordinate issuing authorities. The first issues technology certificates, the second user certificates.
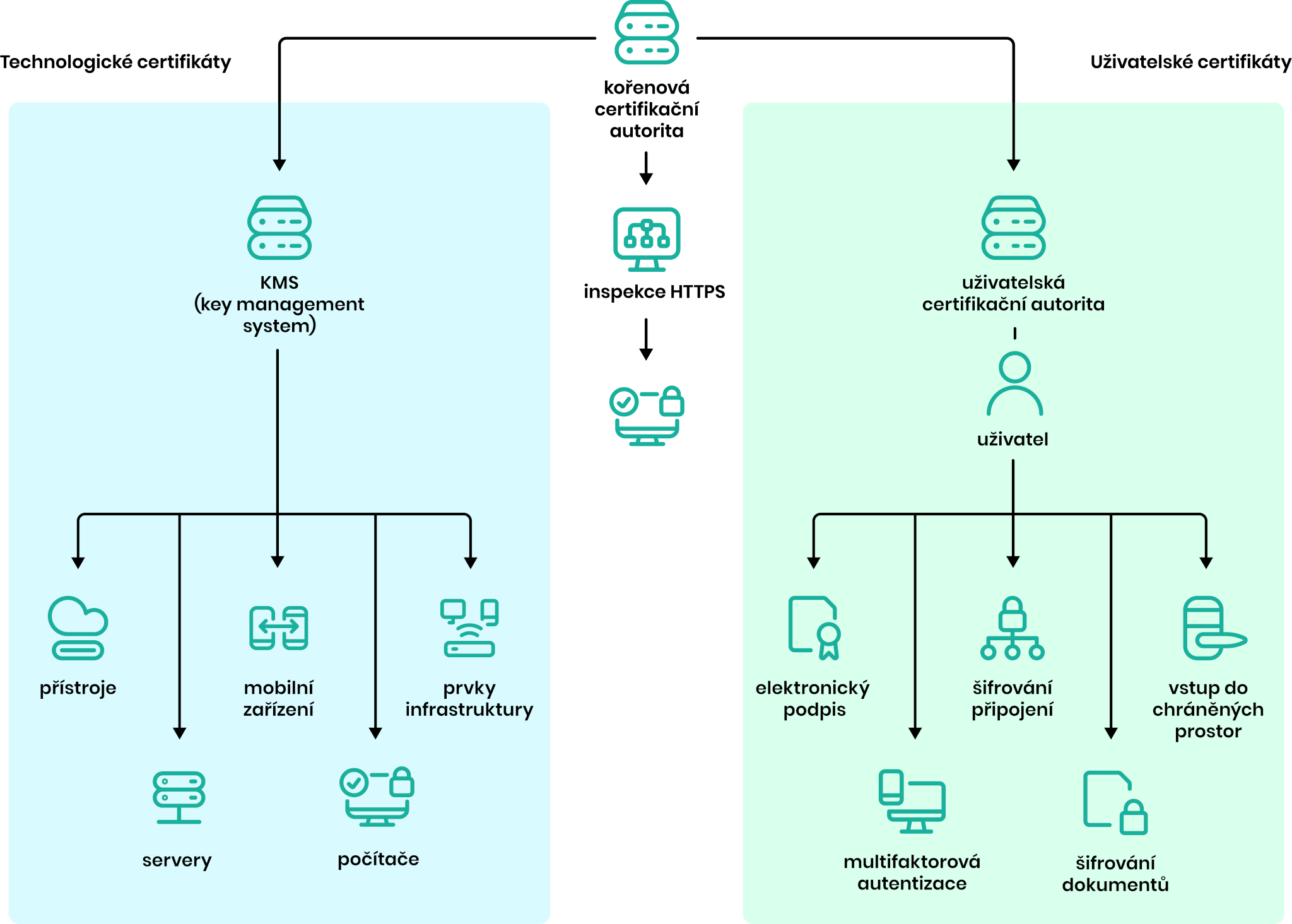

The foundation of an organization’s trust infrastructure is the certification authority (CA). It manages the entire life cycle of certificates – from issuance to invalidation or expiration in the event of an employee leaving or a security incident. Our solution is two-layered. It is based on a separate root CA and separate, issuing CAs (user and system).
The ProID platform supports both user certificates (e.g. for creating electronic signatures) and technology certificates (e.g. for communication between devices and the server), all with connections to authentication tools and add-on modules.
Free brochure:
Learn all about PKI technology, add-on solutions and modern digital identity in a detailed brochure.


Securing an organization’s infrastructure isn’t just about technology – it’s also about processes. Therefore, we also supply all the necessary documents for our solutions. These include, in particular, operating documentation, emergency documentation and certification implementation directives.
Our certification policies define how certificates are issued, managed, revoked and all other activities. They are issued for each type of certificate. They also define what to do in the event of an accident or safety incidents.

Our projects also include a hardware solution for infrastructure – delivery and setup of custom HSM modules that ensure secure storage of cryptographic keys.
HSMs (Hardware Security Modules) are special servers equipped with high protection features. These prevent access to protected information and ensure the trustworthiness of cryptographic operations.
We can not only deliver and configure these devices, but also connect them to your organization’s ecosystem and PKI infrastructure.
Chancellery of the National Council of the Slovak Republic
University of Žilina
