The ProID platform delivers a best-in-class solution for passwordless authentication, offering unmatched security and flexibility.

What is Zero Trust Networking?
Zero Trust Networking Software is a cutting-edge solution designed to implement the Zero Trust Security Model, which assumes that every user — internal or external — is a potential threat until thoroughly verified. Unlike traditional network security systems that rely on a castle-and-moat architecture, zero trust networking enforces strict access controls and continuous verification at every access point within an organization’s infrastructure.
Why the Zero Trust Model?
Modern organizations are embracing decentralized business models, cloud-first strategies, and hybrid work environments, making traditional perimeter-based security obsolete. Zero trust networking software addresses these challenges by:
- Continuously monitoring network activity and user behavior.
- Enforcing adaptive, context-aware authentication policies.
- Collecting data from access points, behaviors, and traffic logs to provide detailed security insights.
ProID: Revolutionizing Zero Trust Networking
Comprehensive Multi-Factor Authentication (MFA):
- ProID enforces MFA across all company systems, including VPNs, RDP sessions, and cloud-based applications.
- Utilizes adaptive authentication tailored to the user’s behavior, risk profile, and device security status.
Physical and Logical Identity Integration:
- ProID uniquely bridges physical and logical security, linking employees’ access to both digital systems and physical spaces.
- Provides seamless identity verification for on-premises systems, such as door access, alongside digital systems like corporate networks.
Granular Network Access Control:
- Enables fine-grained network segmentation, ensuring users only access the resources and systems required for their roles.
- Implements least-privilege principles to reduce attack surfaces.
Streamlined VPN and RDP Access:
- Simplifies secure remote access by integrating ProID’s robust MFA and adaptive security protocols into VPN and RDP systems.
- Protects remote sessions from unauthorized access and credential-based attacks.

Possibilities of using ProID tools
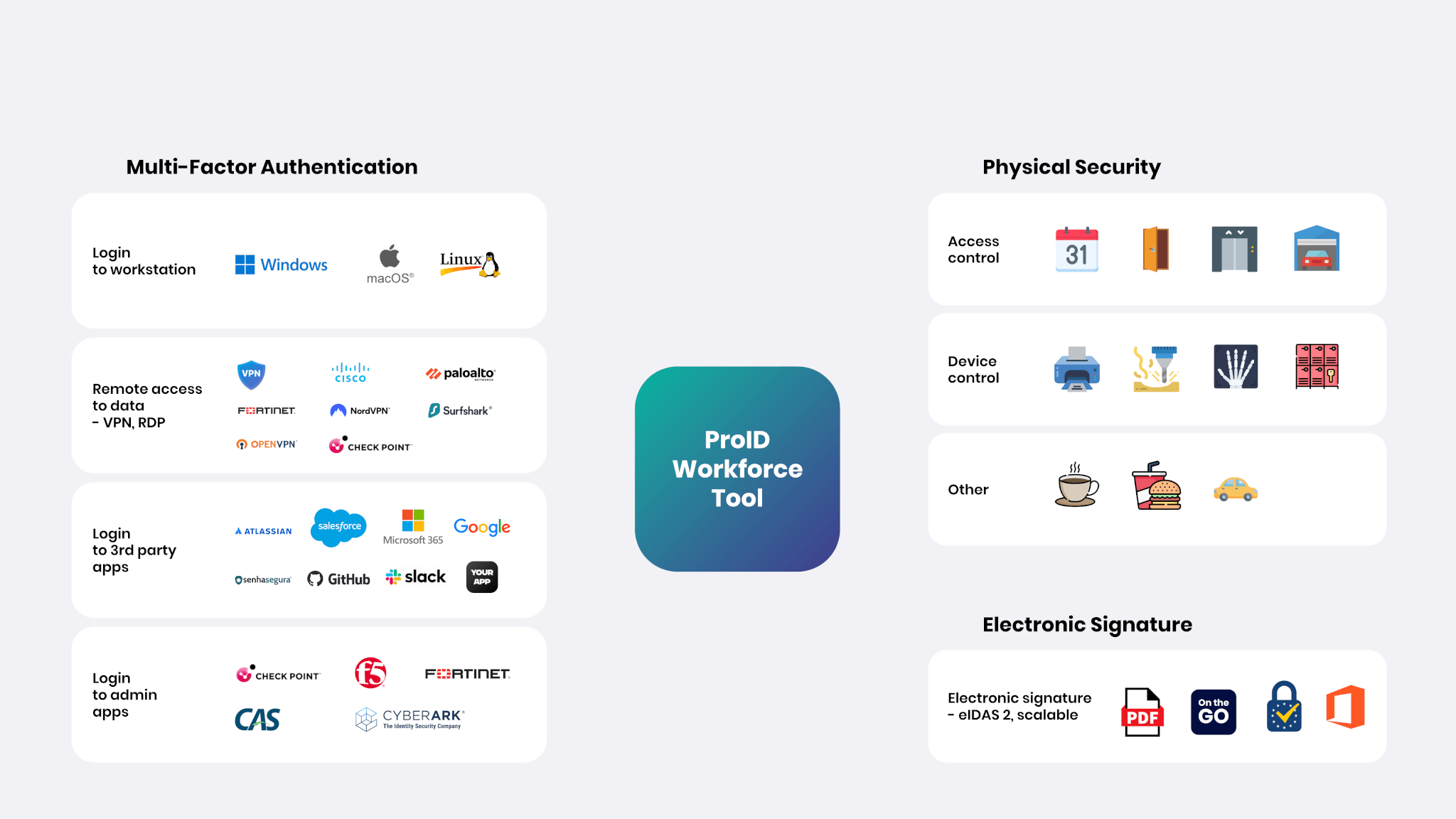
Why choose ProID Zero Trust Networking
ProID stands out by addressing the complex security needs of modern organizations:
- Seamless MFA Deployment: Extends advanced MFA across all organizational systems, reducing friction for employees while maintaining top-notch security.
- Integrated Physical and Logical Security: Ensures that access to physical spaces (e.g., offices) is as secure and tightly controlled as access to digital systems.
- Scalable and Future-Proof: Adapts to evolving security requirements, from securing hybrid work environments to integrating with advanced cloud platforms.
How ProID Exceeds Expectations
ProID not only meets these criteria but goes further, delivering a comprehensive zero trust solution that integrates MFA, network security, and identity management into a single platform. Its ability to secure all systems — VPNs, RDP, cloud, and physical spaces — makes ProID the ultimate choice for organizations committed to implementing a robust and future-ready zero trust security model.
Are you interested in our solution? Contact us

