PKI infrastructure for qualified electronic signing
Chancellery of the National Council of the Slovak Republic








Secure, encrypted login to systems and computers with two-factor authentication tools.

Encrypt electronic documents with private keys and electronic signatures.

Manage users and their permissions with user certificates and lifecycle management modules.

Many industries are subject to specific standards and directives, which must be met for operating in the segment. We offer a technical solution to help you meet these obligations.
The TISAX industry standard applies to the automotive industry. The aim is to ensure safe work with information and its transmission. Our solutions meet the requirements for the highest level of security in a number of ways.
A new EU cybersecurity strategy. In the Czech Republic alone, it includes over 6,000 companies and organizations. It mandates the mandatory introduction of encryption within organizations and two-factor authentication.
Defines the rules for working with electronic signatures. Our solutions are listed on the European trust list of certified instruments for the highest level of signature and seal (“qualified” level).
They apply to organizations falling under critical infrastructure elements and many others. They, too, require the introduction of two-factor authentication into an organization’s systems and computers.

A secure work identity is the foundation of the ProID solution. Thanks to two-factor authentication and user certificates, only securely identified and authenticated users have access to corporate systems. User accounts are created only by responsible administrators. The creation of user accounts is always subject to the approval process and in the event of an employee’s departure, his accounts are deactivated.
ProID tools also support secure encryption of sent documents or logins to systems (e.g. encrypted login to VPN).
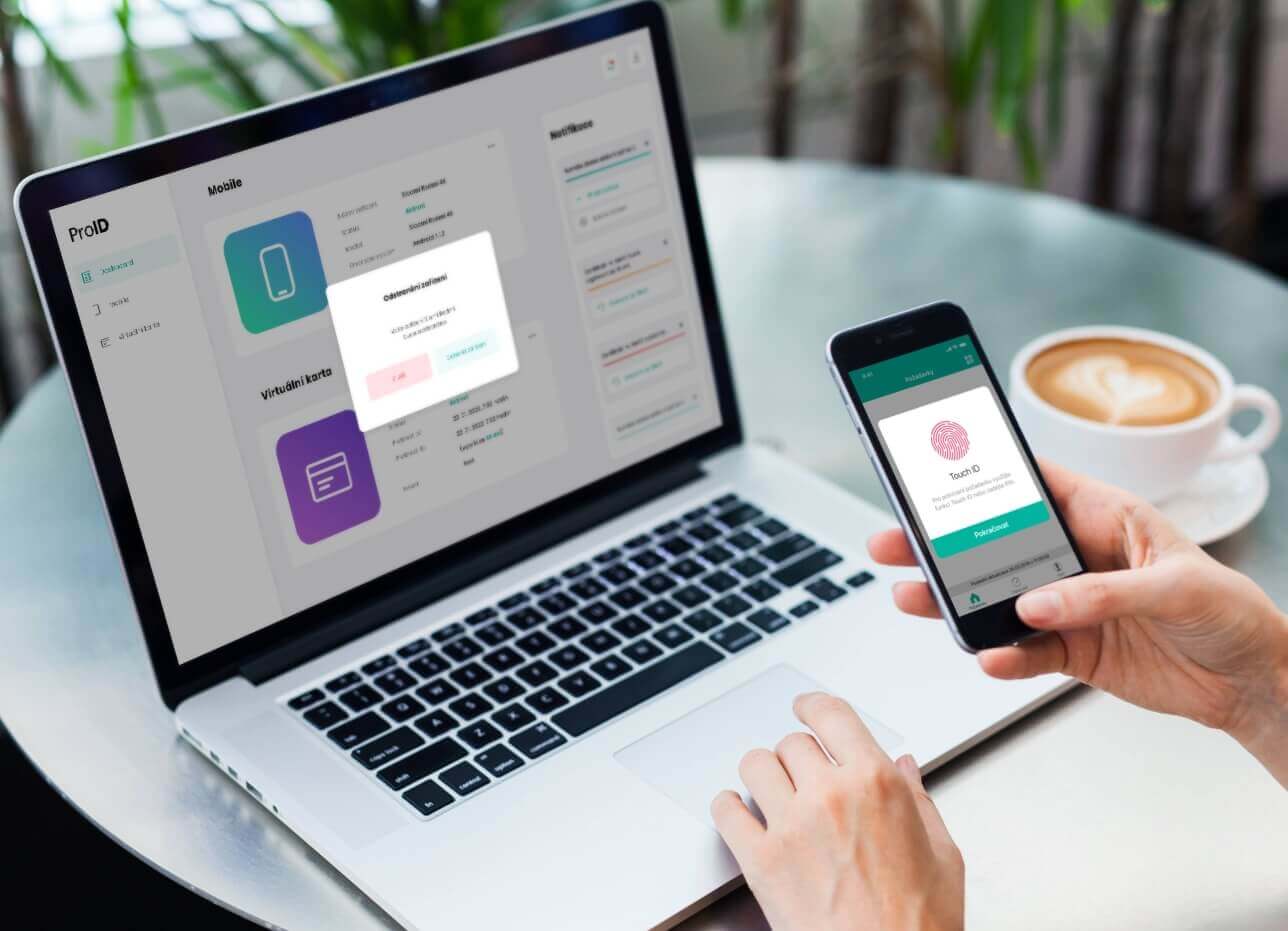
Access rights management in ProID is provided by both authentication tools (smart cards, mobile applications, bittron) and add-on modules for managing the life cycle of these permissions and certificates.
In the ProID platform, a trained person manages users’ access rights using add-on applications. Access rights based on certificates are checked regularly. In addition, logins to systems and devices are encrypted.
Chancellery of the National Council of the Slovak Republic
Erste Group | Česká spořitelna
University of Žilina
