Implementation of the Zero Trust principle
Increase your organisation’s security by implementing Zero Trust principles. Our tools and technology can do the job for you.






A modern organization has its internal perimeter under constant control and verifies every single access. This is Zero Trust.
We develop tools and solutions to help you apply this method. ProID primarily covers the area of digital identity.
![]()
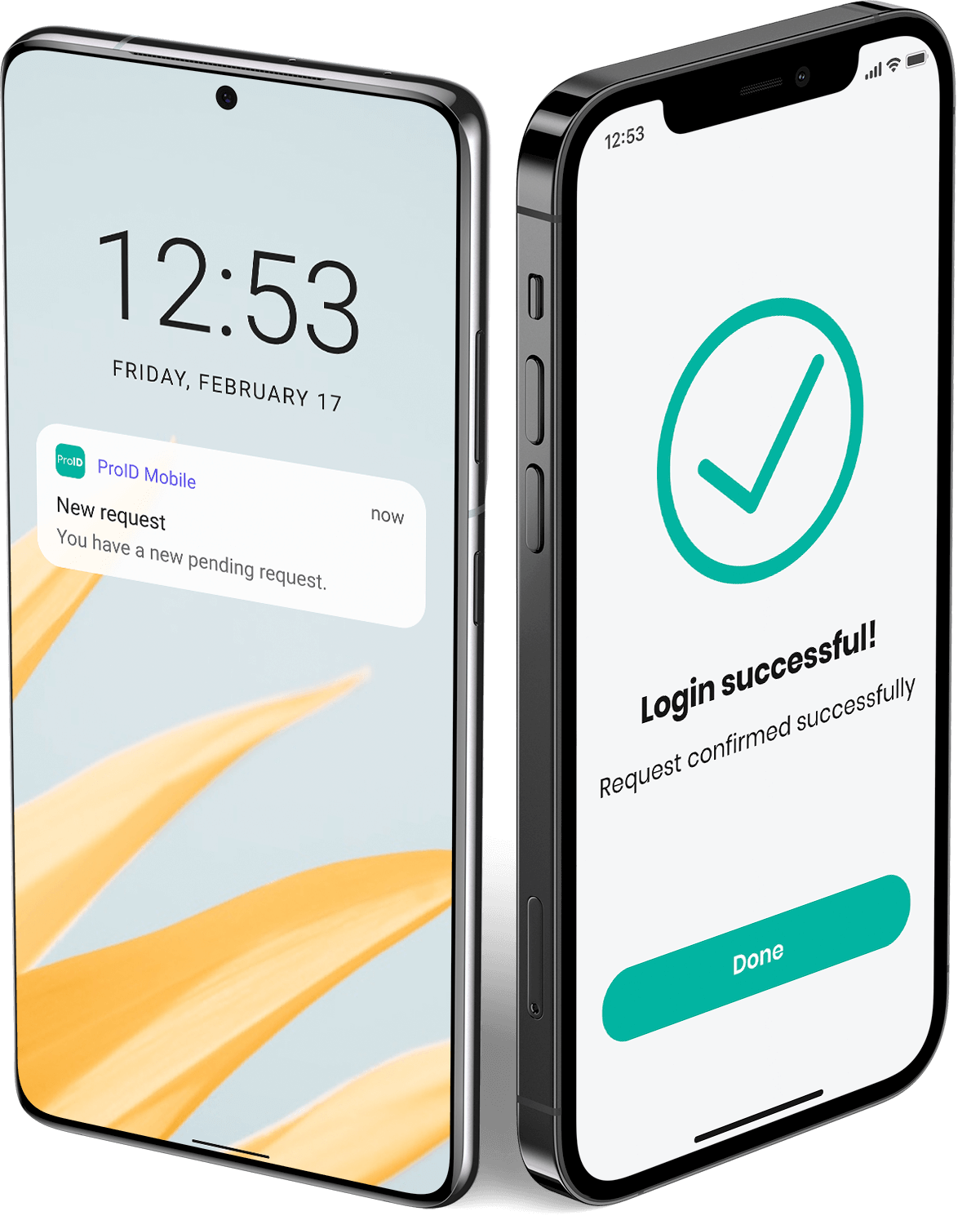
Automatic user verification with each login.

Server and device identity verification every time they connect to the network.

Real-time administration of cryptographic material and digital certificates.

The Zero Trust Principle for internal organizational security
The Zero Trust Security methodology means that every login and every action performed within an organization’s infrastructure is considered untrusted. In order to be executed, it must be authenticated and secured.
The main reason for this approach is the rapid development of digitalization and the multitude of systems in use. More and more employees are also working from home or using various mobile devices. This makes the traditional approach to security obsolete – data and systems can easily be compromised and breached.

Three protection pillars with Zero Trust
Implementing Zero Trust helps to solve basic security issues such as phishing, malware, login compromise, remote access eavesdropping and device vulnerabilities.
The goal is to secure three main points within an organization: users, their devices, and the systems they log into.
- Users can only access the systems they absolutely need to do their job. Each access is preconditioned by multi-factor authentication.
- Endpoints (computers, servers, mobile phones…) are checked and their permissions are verified each time access is requested.
- Applications and infrastructure only allow access to users who have set the necessary permissions, and only from trusted devices.

The ProID platform as part of the Zero Trust implementation
The architecture of the ProID platform is designed so that its individual components support the implementation of the Zero Trust Security method.
- ProID Multifactor is a set of tools for multifactor, single sign-on user logins to computers and clouds.
- The Key Management System (KMS) validates in real-time digital identity of devices, servers and IoT.
- Each login is always checked against current certificates, access without a certificate is not possible.
- The certificate lifecycle is handled by add-on modules to manage certificates and automate complex operations.
- All actions are covered and constantly verified against a system of internal certificate authorities that are physically hosted on HSMs (high security modules).
Interested in our solutions? Contact us