Integration
Multi-factor authentication (MFA) to Check Point
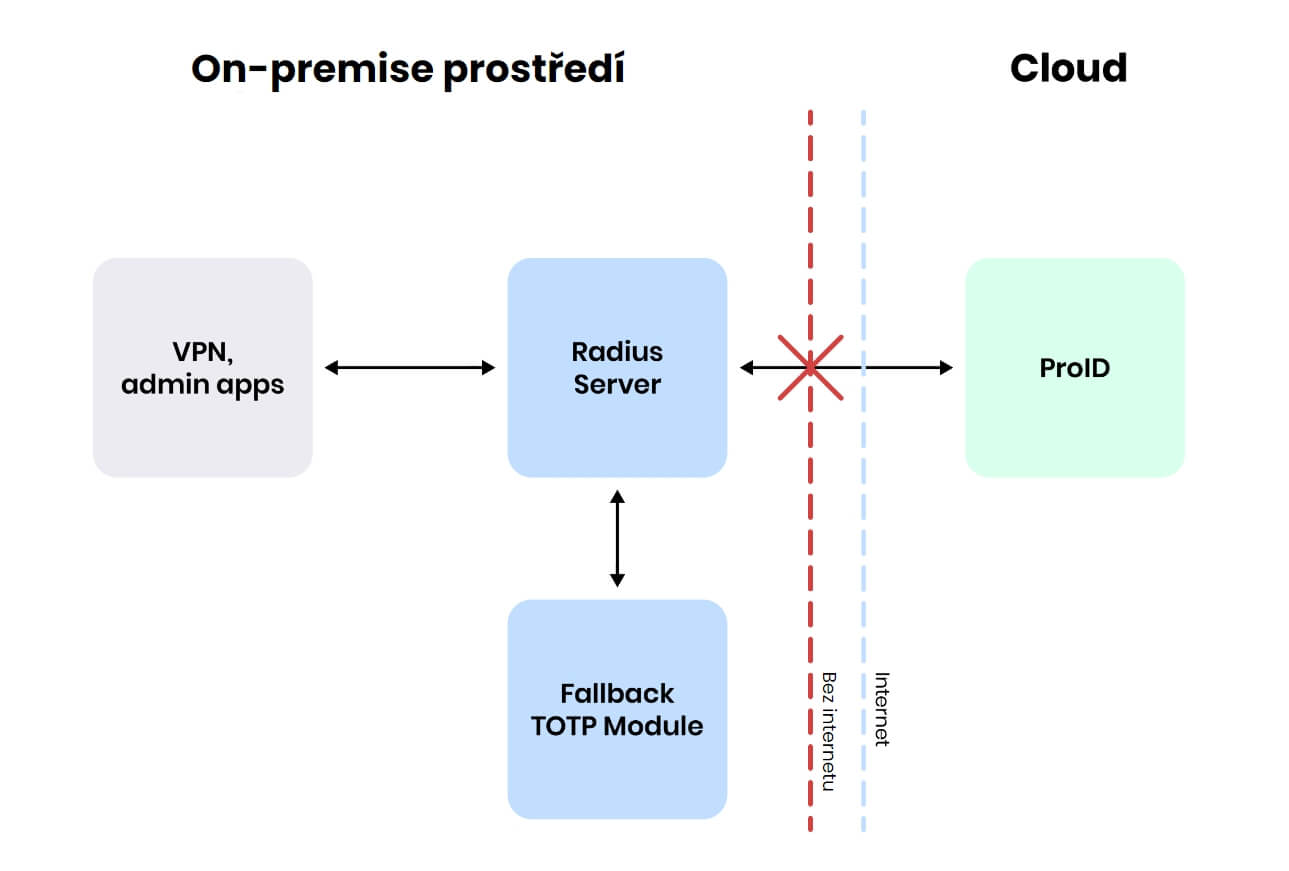
Secure login (MFA/2FA) for admin consoles, management & reporting interfaces, and VPN access via RADIUS


Introduction
Organizations using Check Point Software rely on its advanced network security, firewall, and threat prevention solutions. However, securing admin consoles, management interfaces, and VPN access is crucial to prevent unauthorized access.
With ProID, you can enhance Check Point security by implementing multi-factor authentication (MFA/2FA). Our solution seamlessly integrates with Check Point SmartConsole and VPN via RADIUS, ensuring strong protection without compromising user experience.

What is Check Point?
Check Point Software Technologies is a global leader in cybersecurity, offering next-generation firewalls, endpoint protection, and cloud security. Organizations worldwide use Check Point to protect their networks, applications, and data from cyber threats.
Key solutions include:
- Check Point SmartConsole – A centralized management platform for firewall policies and security monitoring
- Check Point Remote Access VPN – Secure connectivity for remote employees
- Threat Prevention & SandBlast – Advanced security solutions for endpoint and network protection
To ensure that only authorized administrators and employees can access these critical systems, strong MFA authentication is essential.
Common Security Risks:
- Stolen or weak passwords – a common entry point for attackers
- Unprotected admin access – a major risk for enterprise security
- Insecure VPN connections – exposing corporate networks to cyber threats
How ProID Solves Them:
- MFA/2FA for Check Point SmartConsole – Secure admin access and firewall management
- Passwordless authentication – Secure login with smart cards or mobile MFA
- Seamless integration – Works natively with Check Point security policies

Employee Digital Identity you´ve never seen before!
Are You intrested? Register for Free Trial.



Why use ProID with Check Point?
Check Point provides top-tier firewall and threat protection, but without strong authentication, attackers can still breach accounts. ProID ensures that only verified users can access critical Check Point environments, minimizing security risks.
Key Benefits:
- Stronger security for remote access & admin login
- Regulatory compliance (NIS2, GDPR, SOC2, ISO 27001)
- Flexible authentication methods (smart cards, mobile MFA, passwordless login)
- Quick deployment via RADIUS – No complex configuration required
ProID offers full integration of Multi-Factor Authentication (MFA) with Check Point, providing secure remote access and ensuring that only authorized users can connect to corporate networks and security management interfaces.
ProID and OpenVPN Integration
- ProID Mobile enables secure authentication for Check Point using Multi-Factor Authentication (MFA)
- ProID Mobile supports RADIUS authentication using a software token or smart card
- Check Point supports RADIUS authentication for secure remote access and firewall management
Components
- Install ProID RADIUS Proxy (enables communication with the RADIUS-Cloud application)
- Check Point supports RADIUS authentication for secure VPN and admin console login
Interested in Multifactor Authentication and Access Management for your Workforce Security? Register for Free Trial!
System Architecture